IT Services :: Office 4.0
We offer installation and support of all IT equipment for your office and workplaces. We are guided by the six criteria of BIO LOGICAL IT: health, Open Source and Unix, minimizing your IT footprint, best possible IT security, state-of-the-art data security, and maximum independence.
With us, you get everything from a single source: consulting, design, planning, implementation, hosting, and support.
In addition, we certify systems according to BIO LOGICAL IT so that you can be on the safe side.
Apple macOS
We are certified technicians and administrators for Apple and macOS since 2003. We are happy to help you on the subject of Apple Mac.
Linux
We have been working as Linux system administrators, since 1999, with all components, e.g. web servers, databases, mail, DNS and Java/PHP production environments.
BSD Unix
We are FreeBSD, pfSense firewall, VPN and network experts since 2011 and realize any kind of network.
Network Technology
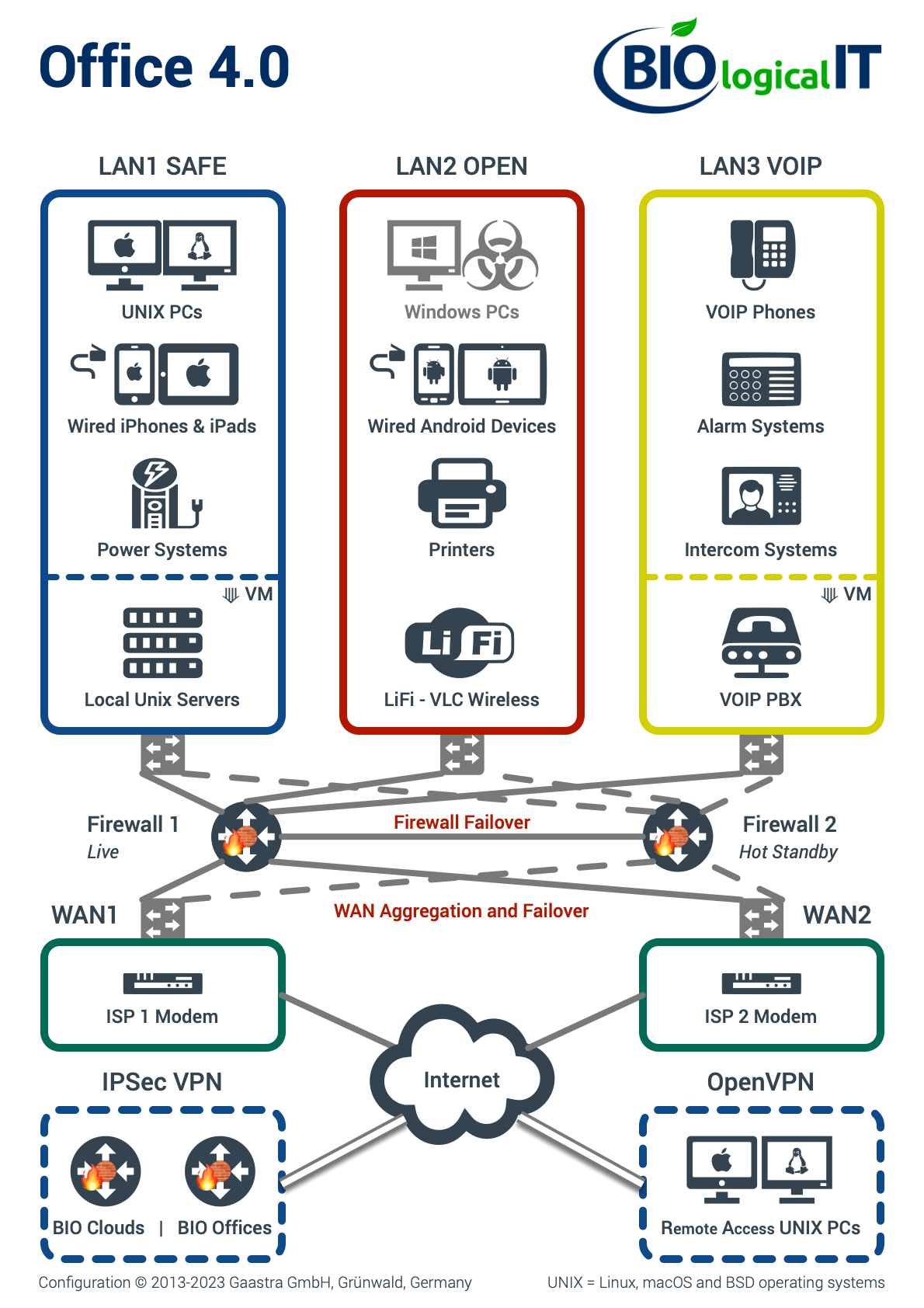
The most basic part of our concept is the setup of your internal network. We use several so-called "subnets" to divide your systems into several network areas with various exactly defined access permissions. This partitioning of the network is precisely controlled by firewalls and switches. This keeps the dangers of a potential attack limited to the respective sub-areas. For example, if you are still using a Windows computer, a resulting ransomware attack could only access the "OPEN" network, while all other parts of the network are secured. (Image below)
Hardware Virtualization
Where possible, we try to configure all server processes together on a small server, with low power consumption, independent of the network area. As an example, we like to configure a high quality VOIP telephone exchange (PBX), a local web server, and a firewall on a "low-power" server. The advantages here are power and space savings, and avoidance of excess hardware. If additional backup is important to you, we can gladly install a second "standby" unit in another, fire-protected area of your building. In this context, we refer to our cloud solutions, so that in the event of a complete loss of your building, your data and applications will still be available.
Firewalls
In the past, we always used Cisco's best technologies in the interest of our customers. Since 2011, however, we have been using the Open-Source-pfSense-Unix-System to secure our networks, for (the) Cloud, virtualized or physical. The benefits are: significantly increased security, more functionality, lower hardware costs, less configuration effort, and less power consumption. In the meantime, we try to avoid closed-source firewalls because the code cannot be seen and, consequently, the processes behind them cannot be verified. For backup, we offer two firewalls with the same configuration, so that if the first firewall fails, the second one automatically takes over.
Multiple Internet Providers
From our experience with DSL, cable, and fiber-optic connections, there are still frequent downtime incidents within Germany. Network downtime, however, can lead to massive revenue losses. Therefore, we recommend corporate customers to keep an additional internet connection of a different type active. If only DSL is available, then internet connections should be via 2 different providers at the same time, e.g. Telekom and O2. When both connections are active, your office has the speed of both connections together! If necessary, we can even combine more than two connections to provide even higher reliability. This way, you will have the Internet running without interruption, unless all connections fail at the same time. For VOIP telephone systems, we consider an additional internet connection a "must". Otherwise, every time your company experiences an internet downtime, telephone communication will also affected. Did you know that VDSL supervectoring works with practically 0 volts? Fail-safe performance is part of the core competence IT security of our BIO LOGICAL IT.
Professional Modems
From the point of view of internet security, you should never use the modem supplied by the internet service provider. With many providers, such as Telekom, there is a so-called "router constraint", whereby the transmission from the Internet to the private network can take place on the supplier's modem - through possible backdoors. Here, the utmost caution is required! However, the router constraint can be bypassed. We consider it much safer to replace the router with a modem, e.g. from Draytek and then perform the transmission over our pfSense firewalls. Such modems actually work only as modems. This approach has the added advantage of making it easier to avoid unwanted wireless local area network (WLAN) and digital enhanced cordless technology (DECT) emissions.
VPN Tunnel
We configure fixed VPN tunnels (IPSec) between your offices and your private cloud servers. VPN tunnels allow you to transfer your data securely over the "Public Internet". We provide you with the safest tunnels currently available (StrongSwan-Community). Key features of the maximum encryption we use are, for example: IKE V2, AES 256, SHA 512, DH-Group 30 and ESP.
For mobile devices, which in our view are best connected to the Internet via cable, we offer VPN tunnels "on demand" (OpenVPN). This way, your employees can connect their laptop, tablet, or smartphone to your offices or your cloud servers with maximum security. With OpenVPN, we can use similarly strong encryption, for example, AES 256, SHA 512, and D-H 4096 bits.
VOIP Telephone Systems
We configure the most modern and secure VOIP PBXs and phones for you. The PBX phone system can be located either in your office, in your private cloud, or at an external service provider. The phones (end devices) are connected to the system via Power-Over-Ethernet in their own protected VOIP network. For the end devices, we recommend "snom" and "Grandstream". We have experience with Asterix-, Sipgate-, and 3CX- systems.
Office and Home Electronics
We integrate and configure your systems for you as desired, preferably via network cables. We try to avoid wireless transmission wherever possible to minimize electrosmog. Our goal is to protect your health and that of your employees from avoidable stress. To ensure maximum data security, devices are always assigned to a separate network part in the network configuration. It is important to us that technical security is always kept at the highest level. We have experience with LED lighting systems, alarm systems, door intercoms, printers, and uninterruptible power supply (UPS) systems from various manufacturers.
Trade Workers
As a BIO LOGICAL IT service provider, we will help you plan, design, connect, configure, and support your systems. Sometimes trade worker services are also required; such as the assembly of a server cabinet or the laying of network cables (in cable ducts or under plaster). Especially for this scope, we maintain some partnerships with competent trade workers who work exactly according to our instructions. This paves the way for sustainable, i.e. BIO LOGICAL IT, in your company.